
With the popularity of market tools to help users detect popular mints, scam contracts have become even more popular. Here are some tips to help you from losing ETH to scams.
The most common scam is copy and pasting a popular project that has yet to release.
Always check the Opensea for a connected Twitter and compare it to the real project's official Twitter.
For example, you can see that the real Myrai (https://twitter.com/MyraiCreations) has not yet minted, but has had imitators release fake contracts (https://opensea.io/collection/myrai-v2).
As you can see, the fake Opensea collection above links to the Twitter "MYRAIOFFICIAL" instead of “MyraiCreations”, and the website leads to a wallet drainer that sets approval for your NFTs and siphons them.
If you ever see ANY website ask to "Set Approval for All" in a Metamask popup, or asks for a signature that prompts red text (seen in the image below), immediately reject the transaction/signature and exit the website.
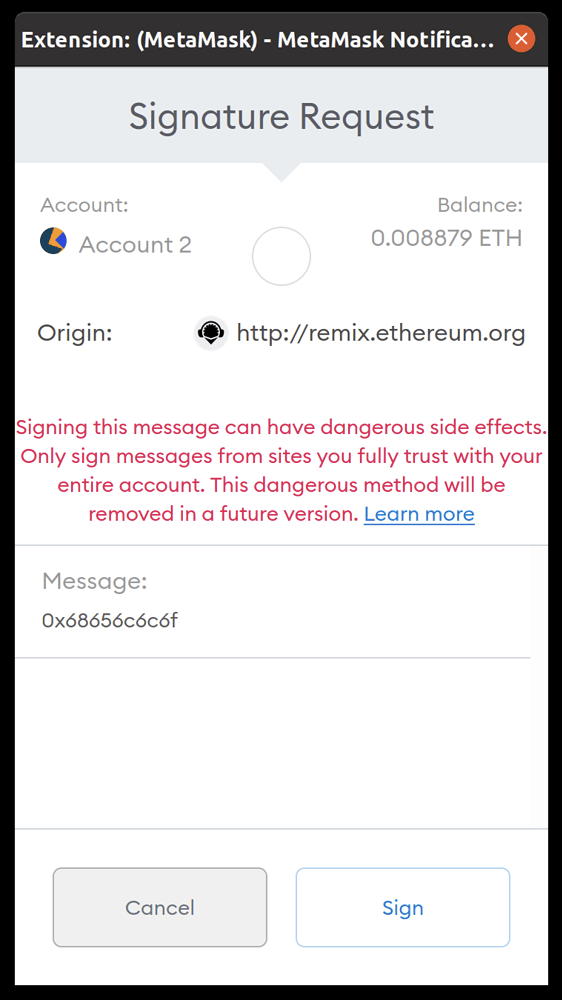
If you think that you may have given the scam your approval, immediately head to https://revoke.cash to remove their approval from the tokens you set. If you've signed a malicious signature, the best course of action is to transfer everything to another wallet immediately.
Another very common scam is when a project claims they've added more supply to their genesis project, or are stealth dropping their new collection. This is almost always fake, do NOT click these links, even if they're posted by the project owner or in the project Discord.
A more recent and advanced scam adds a "signature" to their mint as seen in the picture below. However, the signature is just an epoch timestamp, meaning there is no real purpose for the signature.
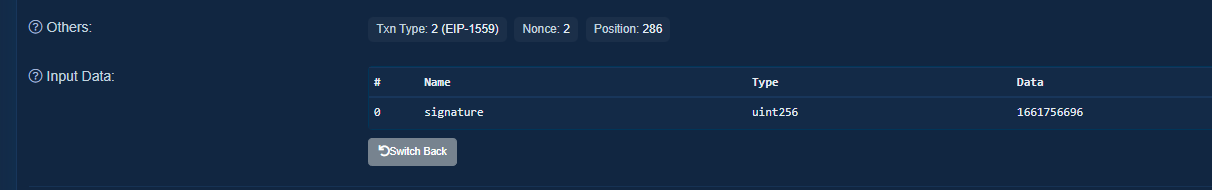
The fake signature tricks less educated minters into going to the website instead of minting from the contract. From there, the website will pop up a set approval or malicious signature, just like the earlier scams would.
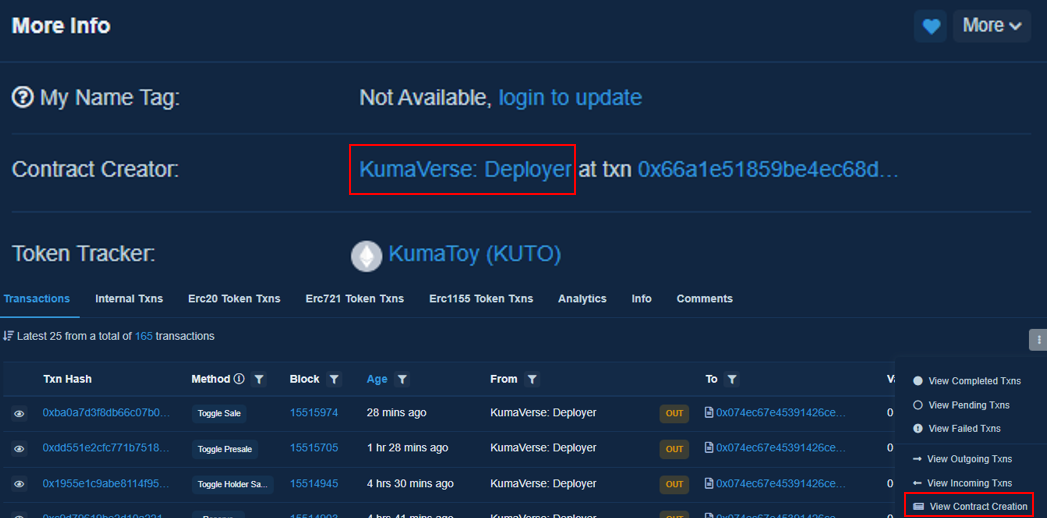
Our final advanced tip for minters identifying scam projects is to always research the contract deployer. Oftentimes these deployers are serial ruggers who have deployed other scam contracts in the past.
The quickest way to do this is to find the contract's deployer at the top right of the etherscan page, then clicking the 3 dots and clicking "View Contract Creation" as seen in the image below.
The Underground contract embed tool within our discord, not only allows users to easily see a plethora of information about the contract including the deployer, but also warns users if "setMaxSupply" exists in the contract.
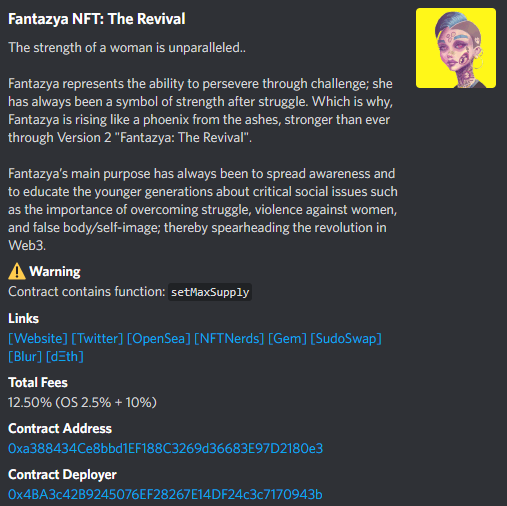
Using the setMaxSupply is a common tactic used by ruggers to increase the max supply of the project after OOS to allow more minting and extract more ETH.
Safety always comes first! Share your other Web 3.0 security tips and tag us on Twitter.





